I have been doing a fair amount of work lately with Fabric Notebooks.
I am always conscious to ensure that when I am authenticating using a Service Principal, I can make sure it is as secure as possible. To do this I have found that I can use the Azure Key Vault and Azure identity to successfully authenticate.
By using the Azure Key Vault I do not have to store any details in clear text.
Another advantage of the Azure Key Vault is that when my client secret expires (every 2 years), I will just have to update the secret in the key vault and everything else will get the new value. This is way easier than trying to remember where I used the service principal account.
Below is how to authenticate with Service Principal using Azure Key Vault.
All the additional details are included in the comments below. The rest of the code is the default details for the authentication.
#########################################################################################
# Read secretes from Azure Key Vault
#########################################################################################
## This is the name of my Azure Key Vault
key_vault = "https://fourmoomoomoo.vault.azure.net/"
## I have stored my tenant id as one of the secrets to make it easier to use when needed
tenant = mssparkutils.credentials.getSecret(key_vault , "myteantid")
## This is my application Id for my service principal account
client = mssparkutils.credentials.getSecret(key_vault , "applicationid")
## This is my Client Secret for my service principal account
client_secret = mssparkutils.credentials.getSecret(key_vault , "cs")
#########################################################################################
# Authentication - Replace string variables with your relevant values
#########################################################################################
import json, requests, pandas as pd
import datetime
try:
from azure.identity import ClientSecretCredential
except Exception:
!pip install azure.identity
from azure.identity import ClientSecretCredential
# Generates the access token for the Service Principal
api = 'https://analysis.windows.net/powerbi/api/.default'
auth = ClientSecretCredential(authority = 'https://login.microsoftonline.com/',
tenant_id = tenant,
client_id = client,
client_secret = client_secret)
access_token = auth.get_token(api)
access_token = access_token.token
## This is where I store my header with the Access Token, because this is required when authenticating
## to the Power BI Admin APIs
header = {'Authorization': f'Bearer {access_token}'}
print('\nSuccessfully authenticated.')
header = {'Authorization': f'Bearer {access_token}'}
## Below is an example where I am querying the datasets Admin API and I need the access token in the
## headers
base_url="https://api.powerbi.com/v1.0/myorg/"
refreshables_url = "admin/datasets"
refreshables_response = requests.get(base_url + refreshables_url, headers=header)
df = refreshables_response.content
display(df)
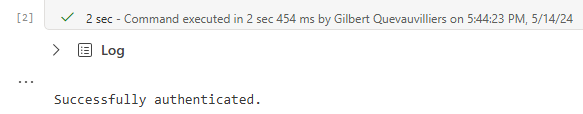
I then run the code and as shown below it is successfully authenticated.
I can then continue with my notebook code using the Power BI Admin APIs, as shown below the display from the df
In this blog post I have shown you how I authenticated using the Azure Key Vault and then successfully querying a Power BI Admin API.
I hope that you found this useful and as always thanks for reading.
You can download the Notebook code here: Azure Key Vault Auth with Service Principal.ipynb



Be the first to comment